[ad_1]

For months, members of Conti—among the many most ruthless of the handfuls of ransomware gangs in existence—gloated about publicly sharing the info they stole from the victims they hacked. Now, members are studying what it’s wish to be on the receiving finish of a serious breach that spills all their soiled laundry—not simply as soon as, however repeatedly.
The unfolding sequence of leaks began on Sunday when @ContiLeaks, a newly created Twitter account, began posting hyperlinks to logs of inner chat messages that Conti members had despatched amongst themselves.
Two days later, ContiLeaks printed a new tranche of messages.
Burn it to the bottom
On Wednesday, ContiLeaks was again with more leaked chats. The most recent dispatch confirmed headers with dates from Tuesday and Wednesday, a sign that the unknown leaker continued to have entry to the gang’s inner Jabber/XMPP server.
“Howdy, how are issues with us?” a Conti employee known as Tort wrote in a Wednesday message to a gang colleague named Inexperienced, based on Google Translate. Tort went on to report that somebody had “deleted all of the farms with a shredder and cleaned the servers.” Such a transfer prompt that Conti was dismantling its appreciable infrastructure out of worry the leaks would expose members to legislation enforcement investigators all over the world.
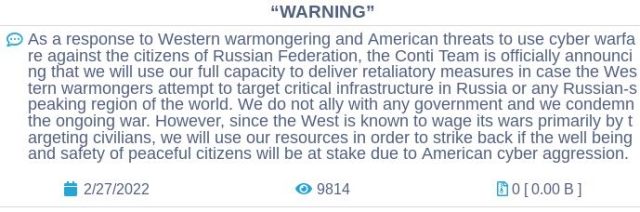
In another tweet, ContiLeaks wrote, “Glory for Ukraine!” This implied that the leak was motivated, at the very least partially, to reply to an announcement posted to Conti’s website on the darkish internet that group members would “use our full capability to ship retaliatory measures in case the Western Warmongers try to focus on important infrastructure in Russia or any Russian-speaking area of the world.”
KrebsOnSecurity, citing Alex Holden, the Ukrainian-born founding father of the Milwaukee-based cyber intelligence agency Maintain Safety, has reported that the ContiLeaks is a Ukrainian safety researcher. “That is his solution to cease them in his thoughts at the very least,” KrebsOnSecurity provides. Different researchers have speculated that the leaker is a Ukrainian worker or enterprise affiliate of Conti who broke with Conti’s Russia-based leaders once they pledged help for the Kremlin.
In all, the leaks—that are archived right here—chronicle virtually two years’ value of the group’s interior workings. On September 22, 2020, as an illustration, a Conti chief utilizing the deal with Hof revealed that one thing seemed to be terribly mistaken with Trickbot, a for-rent botnet that Conti and different crime teams used to deploy their malware.
“The one who made this rubbish did it very nicely,” Hof wrote whereas poring over a mysterious implant somebody had put in to trigger Trickbot-infected machines to disconnect from the command and management server that fed them directions. “He knew how the bot works, i.e. he most likely noticed the supply code, or reversed it. Plus, he one way or the other encrypted the config, i.e. he had an encoder and a non-public key, plus uploaded all of it to the admin panel. It’s just a few type of sabotage.”
There can be panic… and groveling
Seventeen days after Hof delivered the evaluation, The Washington Publish reported that the sabotage was the work of the US Cyber Command, an arm of the Division of Protection headed by the director of the Nationwide Safety Company.
As Conti members tried to rebuild their malware infrastructure in late October, its community of contaminated methods immediately mushroomed to incorporate 428 medical amenities within the US, KrebsOnSecurity reported. The management determined to make use of the chance to reboot Conti’s operations by deploying its ransomware concurrently to well being care organizations that had been buckling beneath that pressure of a worldwide pandemic.
“Fuck the clinics within the USA this week,” a Conti supervisor with the deal with Goal wrote on October 26, 2020. “There can be panic. 428 hospitals.”
Different chat logs analyzed by KrebsOnSecurity present Conti employees grumbling about low pay, lengthy hours, grueling work routines, and bureaucratic inefficiencies.
On March 1, 2021, as an illustration, a low-level Conti worker named Carter reported to superiors that the bitcoin fund used to pay for VPN subscriptions, antivirus product licenses, new servers, and area registrations was quick by $1,240.
Eight months later, Carter was as soon as once more groveling.
“Howdy, we’re out of bitcoins,” Carter wrote. “4 new servers, three vpn subscriptions, and 22 renewals are out. Two weeks forward of renewals for $960 in bitcoin 0.017. Please ship some bitcoins to this pockets, thanks.”
[ad_2]
Source link

